Sponsored by DefenseStorm
Sponsored by DefenseStorm
The Anatomy of a Stellar CISO; From Risk-Taker to Innovator
Sponsored by Vasco
The Changing Role of Technology within the Healthcare Sector
Sponsored by RSA
Putting Fraud Out of Business - PSD2 Readiness and Compliance
Sponsored by Onapsis
Uncovering the Risk of SAP Cyber Breaches
Sponsored by Onapsis
Onapsis Business Risk Illustration
Sponsored by Onapsis
SANS White Paper - Blueprint for CIS Control Application: Securing the SAP Landscape
Sponsored by Spirent
Why Real Testing Requires Emulation, Not Just Simulation for Layer 4-7
Sponsored by VMWare
Why Micro-segmentation Matters Now
Sponsored by Sophos
The Evolution of Ransomware
Sponsored by Happiest Minds
An Approach towards Integrated Cyber Security
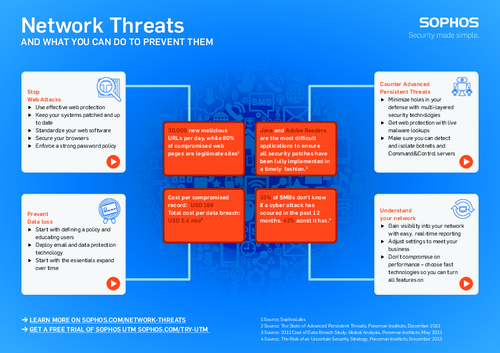
Sponsored by Sophos
Network Threats and What You Can Do to Prevent Them
Sponsored by SAS