Sponsored by BeyondTrust
Sponsored by BeyondTrust
BeyondTrust: Cybersecurity Insurance Checklist
Sponsored by BeyondTrust
BeyondTrust: The Annual Microsoft Vulnerabilities Report 2021
Sponsored by BeyondTrust
BeyondTrust: Buyer’s Guide for Complete Privileged Access Management (PAM)
Sponsored by BeyondTrust
The Guide to Multi-Cloud Privilege Management
Sponsored by BeyondTrust
2022 Cybersecurity Survival Guide
Sponsored by BeyondTrust
BeyondTrust: The Malware Threat Report 2021
Sponsored by Auth0
Privacy and Security - The Journey From Policy to Controls
Sponsored by Duo Security
From MFA to Zero Trust: A Five-Phase Journey to Securing the Workforce
Sponsored by Duo Security
Anatomy of a Modern Phishing Attack
Sponsored by Duo Security
Protecting Against Ransomware: Zero Trust Security for a Modern Workforce
Sponsored by ISACA
To Pay or Not to Pay? Proven Steps for Ransomware Readiness
Sponsored by Menlo Security
Stop Malware for Good: A New Game Plan for Securing Federal Agencies
Sponsored by Menlo Security
Ransomware: State & Local Governments Fight Back
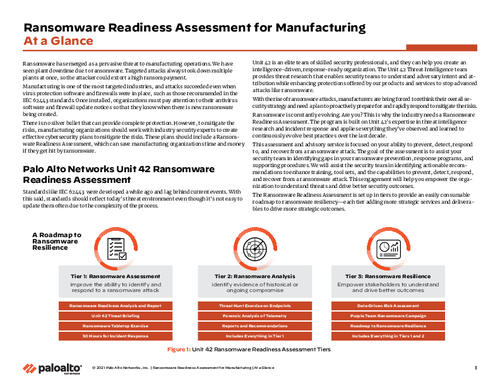
Sponsored by Palo Alto Networks