Sponsored by WatchGuard
Sponsored by LogMeIn
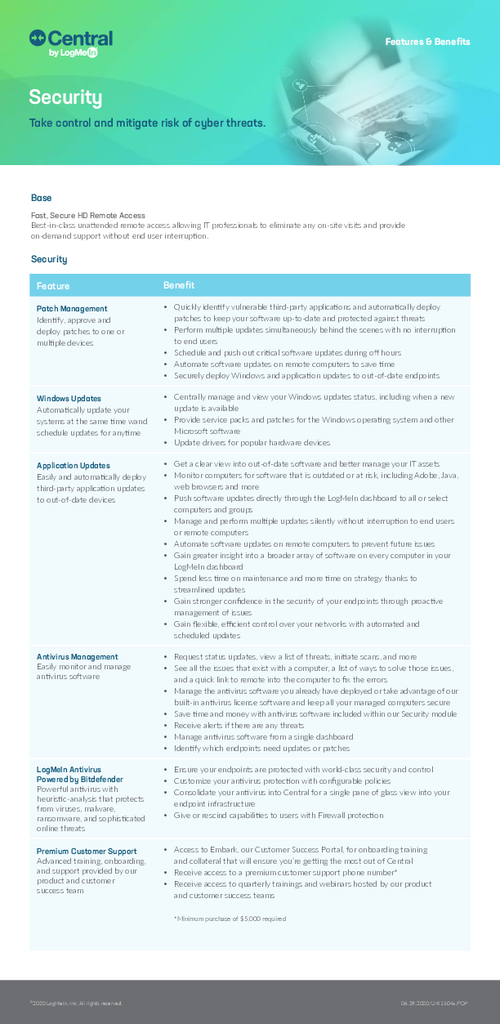
Central Security Module Overview
Sponsored by LogMeIn
How Central and Rescue Work Together for Better Support
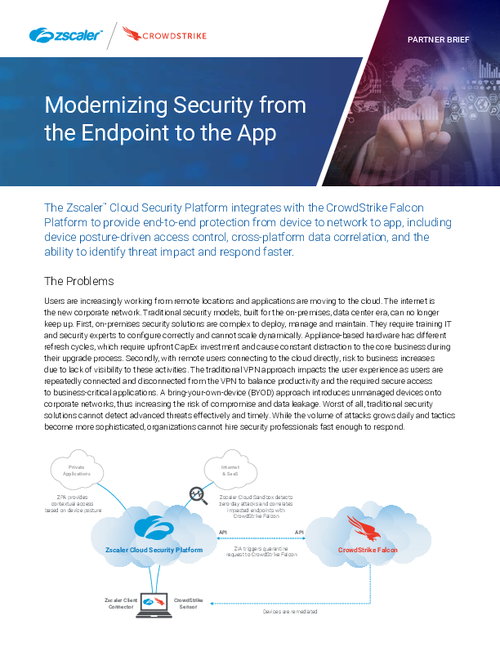
Sponsored by CrowdStrike & Zscaler
Modernizing Security from the Endpoint to the App
Sponsored by McAfee
The Future of Network Security Is in the Cloud
Sponsored by McAfee
Enterprise Supernova: The data dispersion Cloud Adoption and Risk Report
Sponsored by McAfee
MVISION Unified Cloud Edge
Sponsored by Splunk
The Essential Guide to Data
Sponsored by HCL
Embrace the Development and Security Powers of IAST
Sponsored by Radware
How to Keep APIs Secure from Bot Cyberattacks
Sponsored by Sysdig
Container Usage Snapshot
Sponsored by Synopsys
Modern Application Development Security
Sponsored by Rapid7
Industry Cyber-Exposure Report: Deutsche Börse Prime Standard 320
Sponsored by CrowdStrike