Sponsored by CyberArk
Sponsored by Cisco
Guide: How to Get Full Visibility Across Your Infrastructure
Sponsored by Keysight
The Security Testing Imperative
Sponsored by HCL BigFix
The 5 Step Approach to Alleviate Endpoint Management Tool Sprawl
Sponsored by HCL BigFix
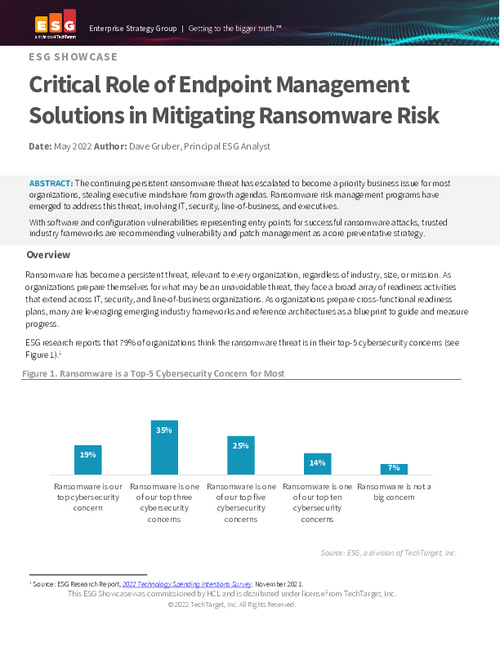
Ransomware Preparedness: The Critical Roles of Endpoint Management & NIST Framework
Sponsored by IBM
Forrester: Total Economic Impact Of IBM Spectrum Scale
Sponsored by Adlumin
The Ultimate Guide to Malware
Sponsored by Perforce Software
2022 State of Automotive Software Development Report
Sponsored by Abnormal Security
2021 Gartner Market Guide for Email Security
Sponsored by Perforce
Which Software Quality Metrics Matter?
Sponsored by Klocwork
Coding Errors: The Cause of 90% Software Security Problems
Sponsored by Klocwork
Top 10 Embedded Software Cybersecurity Vulnerabilities
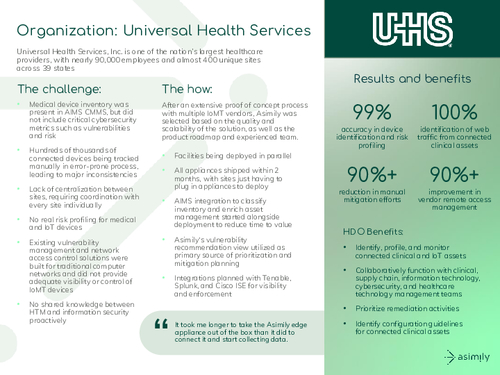
Sponsored by Critical Insight & Asimily