Endpoint Security , Incident & Breach Response , Internet of Things Security
Researchers Identify New Way to Detect IoT Device Malware
Stealthy Malware Found by Harnessing Devices' Electromagnetic Field Emanations
As staff increasingly work from home and connect to networks using internet of things devices, researchers have found a new way of detecting malware on IoT devices. The method leverages electromagnetic field emanations and can detect stealthy malware on the devices even in the presence of obfuscation techniques, report cybersecurity researchers Duy-Phuc Pham, Damien Marion, Matthieu Mastio and Annelie Heuser, from France’s Research Institute of Computer Science and Random Systems. Their findings were presented at the Annual Computer Security Applications Conference held online last month.
See Also: Taking Off with IoT
"Our method does not require any modification on the target device and moreover, our approach has the advantage that it can hardly be detected and evaded by the malware authors," the researchers say.
"Using our approach, a malware analyst is able to obtain precise knowledge about malware type and identity, even in the presence of obfuscation techniques which may prevent static or symbolic binary analysis," they say, and add that during their training phase, they recorded nearly 100,000 measurement traces from an IoT device infected by various in-the-wild malware samples and realistic benign activity.
A Three-Phase Detection Process
The researchers say they use side-channel information to detect anomalies in emanations that differ from previously observed patterns and raise an alert when suspicious behavior is observed that differs from the system's normal state.
This is done, they say, without any on-device modification, and the method enables detection along with classification of kernel-level rootkits, ransomware, distributed denial-of-service botnets such as Mirai, and other benign variants.
The entire detection process works in three phases - data acquisition, data analysis and preprocessing, and malware classification - according to the research document that was viewed by Information Security Media Group.
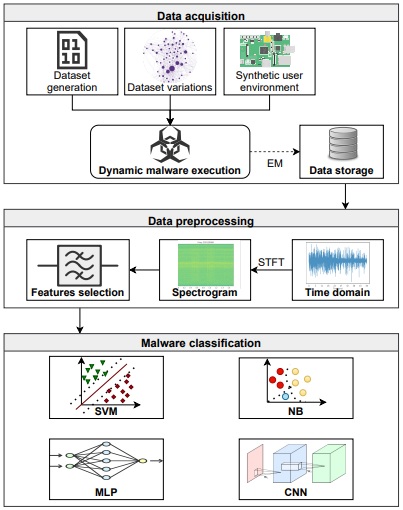
Researchers measured the electromagnetic emanations while executing 30 different malware samples in addition to performing benign activities such as video, music, picture and camera-related activities to train a convolutional neural network - or CNN - model for classifying real-world malware samples, the research paper says.
The framework takes an executable compiled on Linux Raspberry Pi 4.19.57-v7+ ARM as input and exports malware labels using the side-channel information. All executables can be executed directly on the target device, say the researchers, who have categorized the dataset in five different families: bashlite, mirai, gonnacry, rootkit - which includes Keysniffer and MaK_It - and goodware.
Using simple CNN models, the researchers gained all the information regarding the state of the monitored IoT device and then compared it with the normal state of device and finally exported malware labels based on the comparisons made.
To run the experimental setup, the researchers used Raspberry Pi 2B as a target device with 1GB memory and a 900MHz quad-core ARM Cortex A7 processor, with a combination of a PA 303 BNC preamplifier and oscilloscope. With this setup, using the side-channel information approach, the researchers say they successfully detected three generic malware types - and one benign class - with an accuracy of 99.82%.
The researchers say that this methodology works against various code obfuscation/transformations, such as random junk insertion, virtualization and packing, along with a transformation that was previously not known to the system.
To help other malware analysts in applying this methodology for their research and analysis, the researchers have publicly published the resources related to their work on GitHub, which contains the source code, datasets, malware classification models and raw results of the experiments that they conducted to confirm their claims.
IoT Devices an Easy Target
"Consumer IoT devices have always been an easy target," says Pascal Geenens, director of threat intelligence at Radware. He says IoT devices have limited processing power and are not built to be secure by design. "Consumer IoT devices are designed for easy deployment and have the ability to easily expose the device to the internet, thereby providing device users with remote access and connectivity. Most device owners have limited knowledge and awareness of the implications of their actions. This has made consumer IoT a great target for cybercriminals and botnet operators, and this remains the case," Geenens tells ISMG.
"IoT devices are some of the most deployed and internet-exposed devices in the consumer space. Soon botnet operators will start leveraging these devices for DDoS attacks, anonymizing proxies, and in limited ways for crypto-mining, if they have not already begun doing that," he says.
The cost of breaching IoT devices is low, and so is the risk of retaliation or being pursued by security experts, analysts or government agents, Geenens says, and adds that detection techniques such as the one described here might be the way forward for maintaining the hygiene of IoT devices.




















