COVID-19 , Cybercrime , Fraud Management & Cybercrime
Phishing Campaign Spoofs SBA Loan Offer
Malwarebytes Says Campaign Designed to Steal Banking Credentials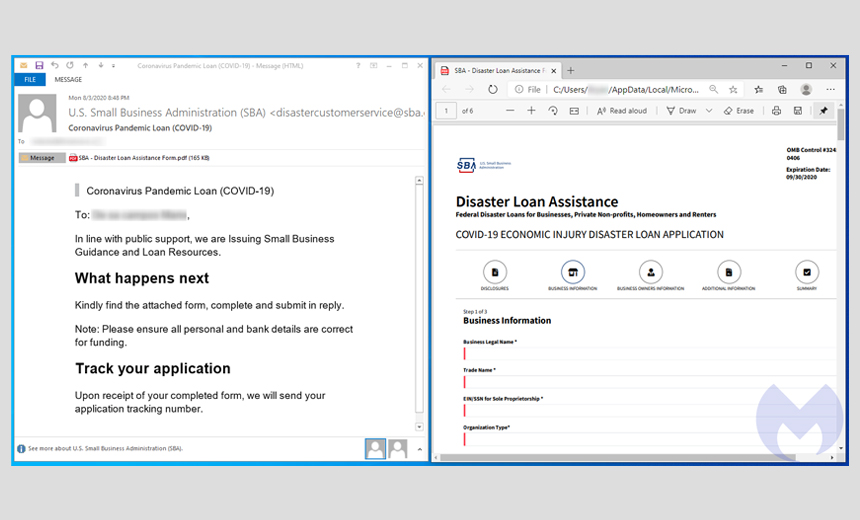
Malwarebytes reports that a newly discovered phishing campaign is spoofing a U.S. Small Business Administration loan offer in an attempt to steal banking credentials and other personal data.
See Also: Splunk Security Predictions 2021
This campaign appears to have started in early August, the security firm reports. Another phishing attack in April also used spoofed SBA messages, but it was created to spread a dropper called GuLoader, which is used to distribute other malware.
Since the COVID-19 pandemic began, the SBA has been overseeing the Payroll Protection Program to help funnel loans to U.S. small businesses that have been disrupted. Fraudsters have used the agency's images and logos as part of fraud campaigns designed to harvest victims' credentials or steal financial information (see: Latest Phishing Campaigns Spoof Federal Reserve, SBA).
The Payroll Protection Program expired in early August. Congress and the Trump administration are discussing whether to continue the program in a new round of stimulus measures, according to USA Today.
Fake Loan Applications
In the phishing campaign that Malwarebytes discovered, the victims are asked to fill out an attached "disaster loan assistance" form that asks for personal as well as banking details. The document spoofs legitimate SBA loan applications.
"This is … a pretty clever and daring scheme that tricks people into completing a full form containing highly personal information, including bank account details," Jerome Segura, director of threat intelligence at Malwarebytes, notes in the report.
SBA Phishing Scheme
The spoofed messages have a legitimate SBA email address embedded in the body of the email, according to the report. But if the victim hits the reply button, they see a slightly different, malicious address. Malwarebytes analysts found that the domain associated with this fraudulent email address, gov-sba[.]us, was registered on July 31 and is not associated with the SBA.
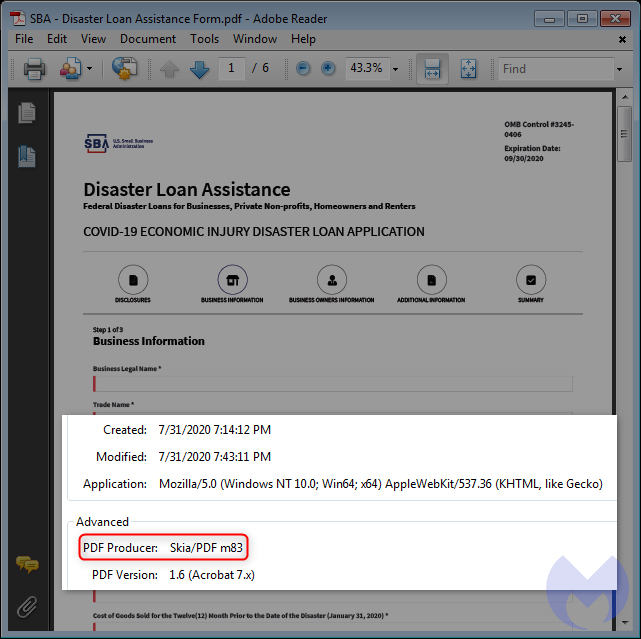
To create the attached fake PDF loan application, fraudsters appear to have downloaded the legitimate loan documents from the official SBA government site and then created their own version. The Malwarebytes report notes that the original was created with Adobe Acrobat, while the spoofed version was designed with an application called Skia - a graphics library for Chrome.
The Malwarebytes report notes that these types of government-backed loan applications are typically printed out and mailed to the SBA and not returned through email.
The fraudsters apparently are attempting to gather information via the loan form that they can then use to commit fraud, the researchers say.
Difficult to Detect Scheme
Because this phishing scam closely spoofs the SBA email address and loan application, it could prove difficult to detect that it’s fraudulent, the Malwarebytes report states.
The security firm recommends that those who receive an email about a loan application should call the SBA to check its legitimacy.
The U.S. Department of Justice and the SBA have published notices warning about such schemes.






















