Card Not Present Fraud , Fraud Management & Cybercrime , Fraud Risk Management
PCI SSC Releases Data Security Standard Version 4.0
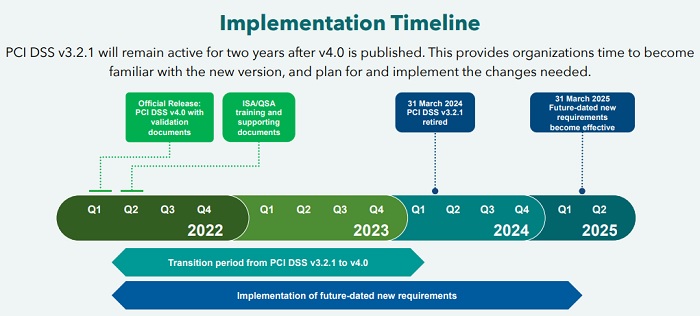
DSS v3.2.1 Active Until March 31, 2024, Then Retired Over 1-Year Period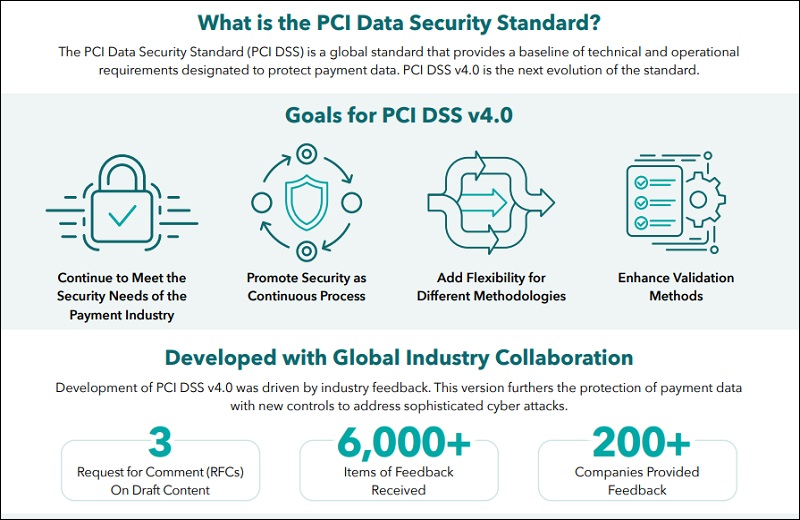
The PCI Security Standards Council on Thursday released the Payment Card Industry Data Security Standard version 4.0. The Council says that the latest version's improvements are intended to counter evolving threats and technologies, and the new version will enable innovative methods to combat new threats.
See Also: Insider Insights for the PCI DSS 4.0 Transition
Organizations currently use PCI DSS version 3.2.1. The council is allowing two years - until March 31, 2024 - for the industry to conduct training and provide education regarding implementation of the changes and updates in version 4.0. While the new standard will be considered best practice, the current version of PCI DSS will remain active during this time. After March 31, 2024, it will be retired over the next year, and the new requirements will become effective after March 31, 2025.
The global payments industry received feedback on the latest changes over the course of three years, during which more than 200 organizations provided more than 6,000 suggestions to ensure the standard continues to meet the ever-changing landscape of payment security, the council says.
"Over the last two years, the PCI Security Standards Council has invited payments industry stakeholders to participate in the development of the new PCI DSS v4.0. The collaborative efforts of many - including participating organizations and qualified security assessors - enabled the standard to provide new flexibility in addressing the requirements' mindful (of) technology advances," says Michael Johnson, executive director at JPMorgan Chase.
Lance Johnson, executive director of the PCI SSC, says, "The industry has had unprecedented visibility into, and impact on, the development of PCI DSS v4.0. Our stakeholders provided substantial, insightful and diverse input that helped the council effectively advance the development of this version of the PCI Data Security Standard."
What Are the Changes?
Emma Sutcliffe, senior vice president and standards officer at PCI SSC, tells Information Security Media Group, "PCI DSS v4.0 is more responsive to the dynamic nature of payments and the threat environment" than the previous version. She says version 4.0 "continues to reinforce core security principles while providing more flexibility to better enable diverse technology implementations" and will "help organizations secure account data now and into the future."
The council says the primary focus of version 4.0 is on keeping up with "the evolving security needs of the payments industry, promoting security as a continuous process, increasing flexibility for organizations using different methods to achieve security objectives and enhancing validation methods and procedures." Other changes cited by the council include:
- Updated firewall terminology to network security controls to support a broader range of technologies used to meet the security objectives traditionally met by firewalls;
- Expansion of Requirement 8 to implement multifactor authentication for all access into the cardholder data environment;
- Increased flexibility for organizations to demonstrate how they are using different methods to achieve security objectives;
- Addition of targeted risk analyses to allow entities the flexibility to define how frequently they perform certain activities, as best suited for their business needs and risk exposure.
Implement Changes ASAP
Tim Erlin, vice president of strategy at Tripwire, says the transition period until the new standard becomes effective in 2025 provides organizations with time to adapt to the new requirements but also leaves room for greater risk.
"Determining the appropriate implementation time frame for new compliance requirements is a balancing act. It would be ideal if most organizations moved to the best practices before they’re required," he tells ISMG.
Erlin says he appreciates the positives in version 3.2.1 but says that it primarily addressed secure configuration and, unfortunately, focused on changing vendor-supplied default passwords. "Secure configuration management goes well beyond vendor-supplied passwords, and it's great to see the new version of the standard take a more expansive approach to the requirement," he says.
Zero Trust: A Welcome Change
Erlin says that the adoption of zero trust architecture has increased since the previous version of the PCI DSS was released in 2018. Earlier this year, the U.S. Office of Management and Budget released a federal strategy to move the U.S. government toward mature zero trust architectures (see: US OMB Releases Zero Trust Strategy for Federal Agencies).
"The new version of the standard makes room for zero trust approaches to authentication and authorization with allowances for "dynamically analyzed" security posture as a mechanism for providing 'real-time access to resources' as an alternative to rotating passwords," Erlin says. "Keeping up to date with best practices in cybersecurity is important in order to avoid organizations downgrading security in order to maintain compliance." He says zero trust could help in maintaining that equilibrium.
In addition to the updated standard, PCI SSC has published in its document library the Summary of Changes from PCI DSS v3.2.1 to v4.0, the v4.0 Report on Compliance Template, the ROC Attestations of Compliance and the ROC Frequently Asked Questions.
The standard and Summary of Changes will soon be translated into several languages to make global adoption of the standard easier. These translations will be published over the next few months, between April and June 2022, the council says.