3rd Party Risk Management , Application Security , Breach Notification
Data Breach Reports Rise as Supply Chain Attacks Surge
US Breach Notification Transparency Declining, Identity Theft Resource Center Warns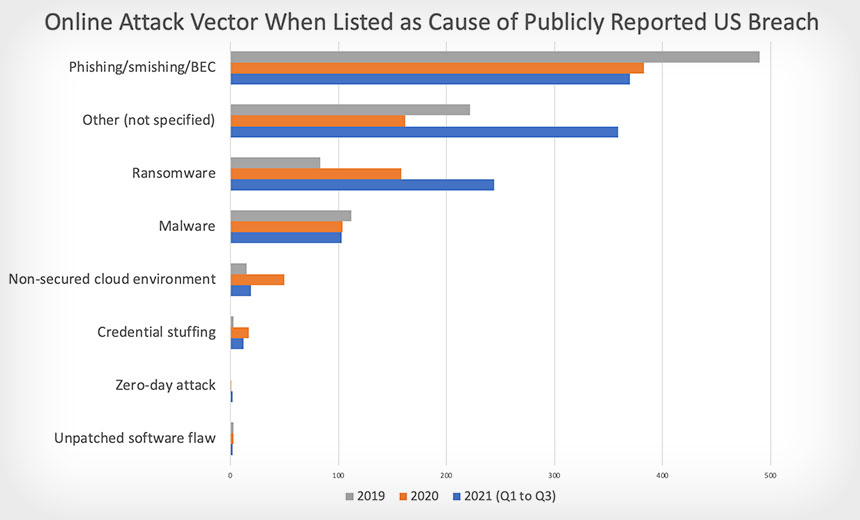
Unwelcome news on the data exposure front: If U.S. data breach notification trends hold steady, expect this year to break records, and not in a good way.
See Also: Cybersecurity for the SMB: Steps to Improve Defenses on a Smaller Scale
The Identity Theft Resource Center, a nonprofit organization based in San Diego, says that in the first three quarters of this year, the number of publicly reported data breaches was 17% higher than what was seen for all of 2020. While the number of breach reports issued this year did decline from Q2 to Q3 by 9%, "the trendline continues to point to a record-breaking year for data compromises," it says.
Blame breaches that trace to online attacks in particular. For the first three quarters of this year, ITRC saw a 27% rise in breaches attributed to online attacks - and especially due to phishing and ransomware - compared with all of 2020.
Another rapidly increasing breach culprit: supply chain attacks.
"Although supply chain attacks only count as a single attack, they impact multiple organizations and the individuals whose data is stored by them," ITRC says. "Sixty entities were impacted by 23 third-party or supply chain attacks, including eight attacks that were reported in previous quarters." The Q3 breach notifications add up to a total of 793,000 more individuals being affected by such attacks.
Supply Chain Attacks
Here's a selection of supply chain attacks that triggered breach notifications, with a count of how many such notifications have so far been released:
- Blackbaud (2020): "The ITRC has recorded 580 entities with 12,813,995 victims from the Blackbaud data breach," which occurred in 2020, it says. Of those 580 breached organizations, 100 of them - with 253,000 customers or users - didn't report being victims until this year;
- CaptureRX: 162 entities affected;
- Accellion File Transfer Appliance: 38 entities affected;
- Netgain Technologies (2020): 23 entities affected by 2020 attack;
- ParkMobile: 19 entities affected;
- Herff Jones: 12 entities affected;
- Med-Data: 6 entities affected.
That isn't necessarily the full count of organizations - aka entities - affected by each supply chain attack. Rather, it represents only victim organizations that have issued a breach report that has become public.
Where supply chain attacks are concerned, expect the number of resulting breaches to increase. The European Union Agency for Cybersecurity, or ENISA, warned in July that it expects to see four times as many supply chain attacks in 2021 as in 2020.
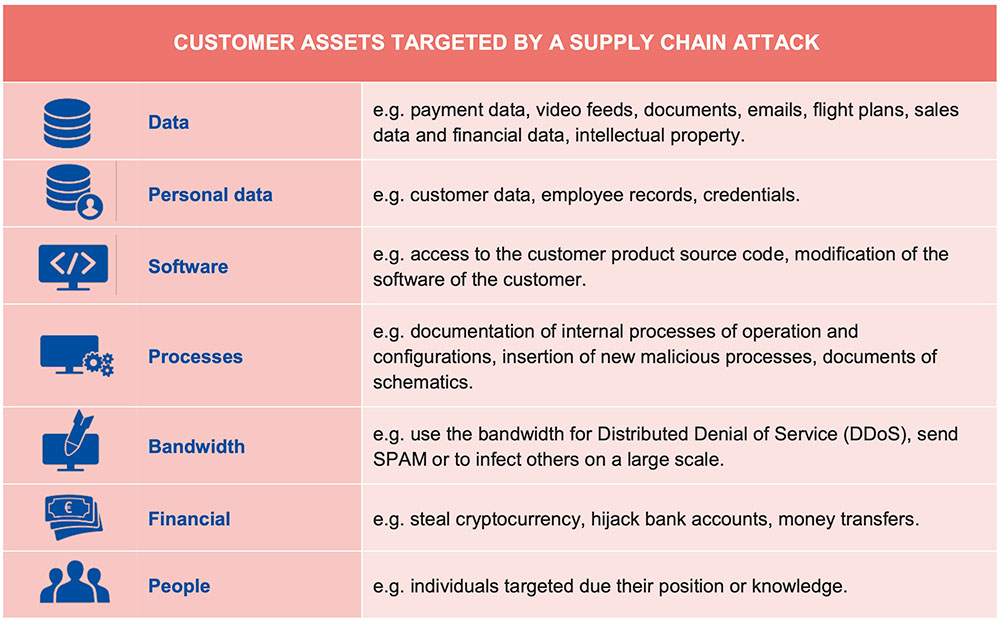
Reviewing 24 supply chain attacks from January 2020 through early July, ENISA found that "around 58% of the supply chain attacks aimed at gaining access to data - predominantly customer data, including personal data and intellectual property - and around 16% at gaining access to people."
Breach Reporting Rules
The key to breach analyses published by the likes of ENISA, and EU data protection agencies or Britain's Information Commissioner's Office, as well as the ITRC in the U.S., remains organizations that suffer an attack disclosing that fact to affected consumers and relevant regulators, and publishing meaningful details to inform victims what steps they should take to protect themselves (see: Data Breach Culprits: Phishing and Ransomware Dominate).
Europe mandates that organizations report breaches involving people's personal information to regulators, who may require them to then inform consumers. Such breaches must be reported to relevant authorities, including their national data protection authority, within 72 hours.
Organizations that fail to follow the rules face the potential of steep fines. GDPR empowers EU regulators to impose fines of up to 4% of an organization's annual global revenue or 20 million euros ($23 million) - whichever is greater - if they violate Europeans' privacy rights, for example, by failing to secure their personal data. Violators can also lose their right to process people's data.
Congress has passed no equivalent legislation to safeguard Americans' privacy or penalize organizations that fail to safeguard people's personal information.
State-level legislation in the U.S. often at least requires breach notifications, but typically only if a breach has affected personal information pertaining to a certain number of consumers - usually, more than 500 individuals. While requirements can vary by sector, including healthcare, which is covered by federal rules, many states don't specify minimum standards for the type of information a notification must contain, or how quickly it must be issued.
Transparency Waning
While security experts have been urging breached organizations to share more details about how they were compromised, not least to help others better protect themselves, as well as to enable consumers to act quickly to protect their privacy, unfortunately, there appear to be multiple moves happening in the opposite direction.
"There is a disturbing trend developing where organizations and state agencies do not include specifics about data compromises or report them on a timely basis," ITRC says. "One state has not posted a data breach notice since September 2020."
ITRC notes that consumers already oftentimes appear reluctant to act on breach notifications to better safeguard their identity, and that such hesitancy is likely to only be exacerbated by organizations failing to alert them to breaches in a timely and robust manner.






















