Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Cybercrime
Mandiant: Attackers' Median Dwell Time Drops to 3 Weeks
80 Zero-Day Vulnerabilities - a Record Number - Were Exploited in the Wild in 2021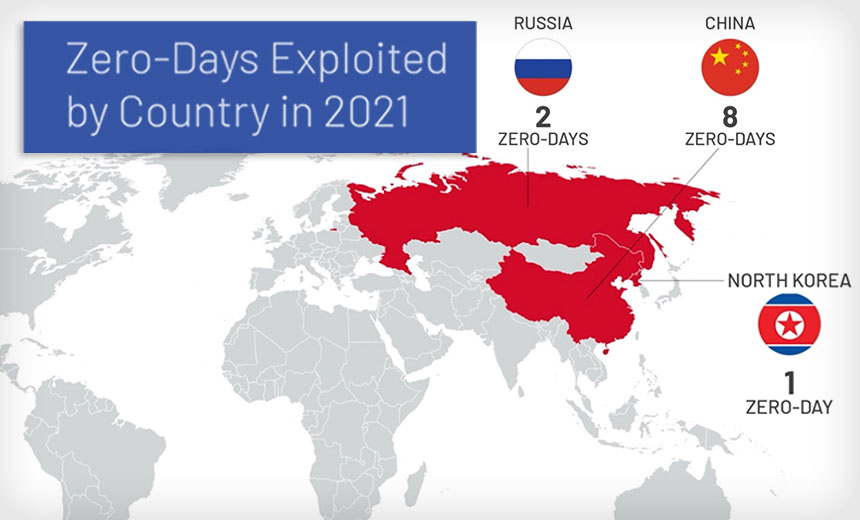
The median number of days an attacker dwells in a system before detection fell from 24 days in 2020 to 21 days in 2021, according to the M-Trends 2022 report by cybersecurity company Mandiant. The biggest year-on-year decline in median dwell time occurred in the APAC region, where it dropped from 76 days in 2020 to 21 days in 2021.
See Also: Modernizing Malware Security with Cloud Sandboxing in the Public Sector
In a separate report detailed below, Mandiant says that the number of zero-days exploited in the wild hit record highs in 2021.
Dwell Time Decline, Threat Detection
For the EMEA region, the median dwell time dropped from 66 days in 2020 to 48 days in 2021, while for the Americas it remained steady at 17 days, the report says.
Yihao Lim, intelligence strategy lead, APJ, Mandiant, tells Information Security Media Group there are several reasons for the decline in dwell time. "Organizations are now more mature in detecting the threats themselves. Secondly, vendors and third-party organizations are more actively sharing threat observations with victims. Thirdly, there is more information sharing between companies, and governments in APAC are taking cybersecurity more seriously now," he says.
Lim also observes APAC governments setting up cybersecurity governing bodies that send guidelines and best practices to organizations. "The APAC countries now have a better understanding and appreciation of the severity of cyberthreats and ... this gives people more awareness and more appreciation of how severe things can be."
Dwell time in the Americas remains steady at 17 days because "the Americas have always been much more mature in terms of cybersecurity awareness and appreciation than other regions. They have maintained their detection," Lim says.
The lowered median dwell times may also be the result of the improved threat visibility and response in organizations, the report says. Another reason for the decline is the pervasiveness of ransomware, which has a significantly lower median dwell time than nonransomware intrusions.
"Ransomware actors are a reason why the numbers dropped because, to them, time is money. They want to make the most money in the shortest time. So they will notify victims as soon as they have achieved their objectives," Lim says.
The report also shows how threats were detected across different regions. In the EMEA and APAC regions, for instance, a majority of the intrusions in 2021 were identified by external third parties - 62% and 76%, respectively. In the Americas, most intrusions - 60% - continued to be detected internally by organizations themselves.
Zero-Day Numbers Soar
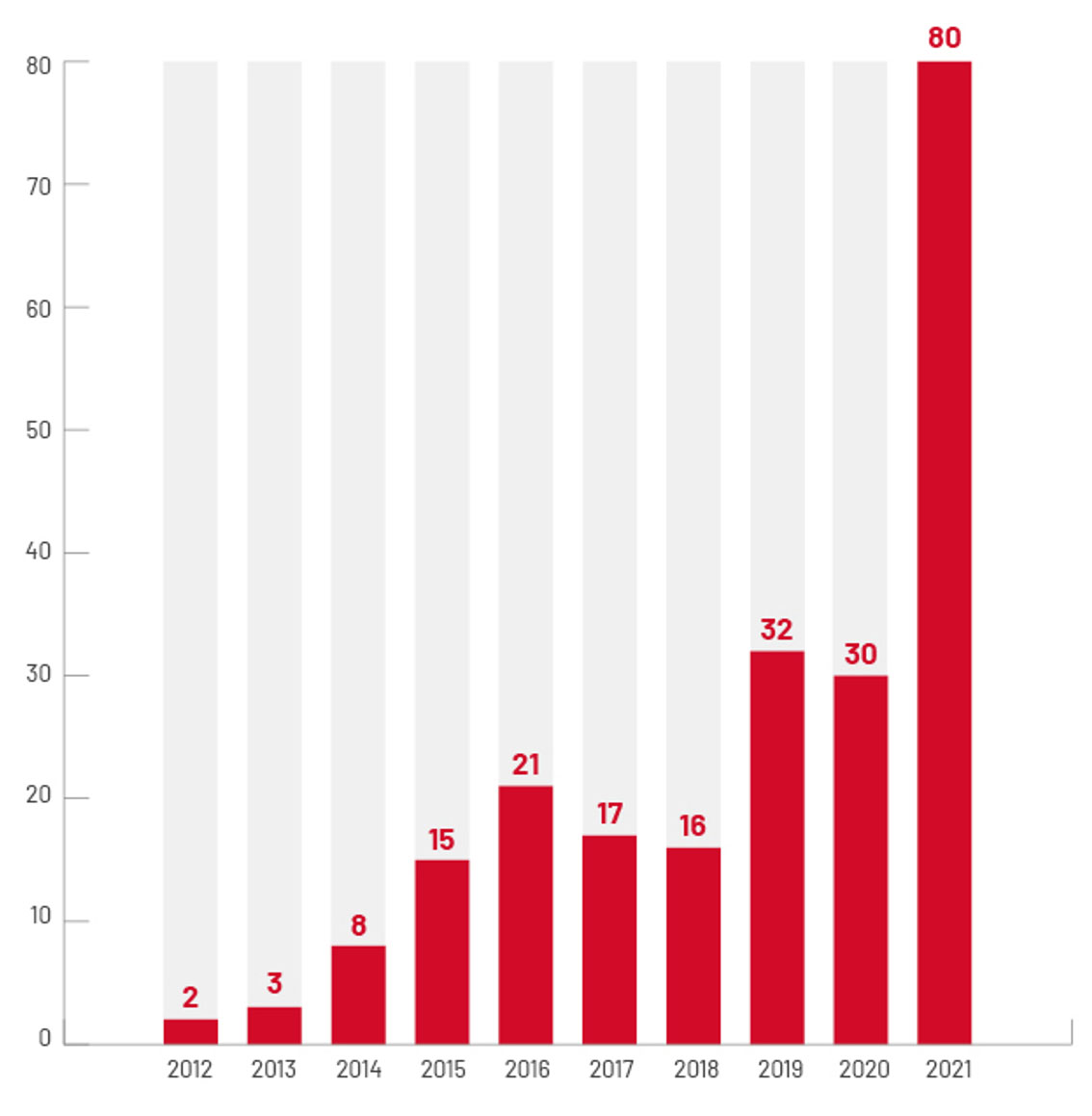
A separate Mandiant threat intelligence report shows that in 2021, 80 confirmed zero-day vulnerabilities were exploited in the wild, a more than twofold increase from the previous record volume in 2019. The report says state-sponsored groups "continue to be the primary actors exploiting zero-day vulnerabilities, led by Chinese groups."
Mandiant says it analyzed more than 200 zero-day vulnerabilities in the wild between 2012 and 2021. This number, it says, makes up 40% of the zero-days analyzed in the past decade. Mandiant cites financially motivated actors as a key reason for this growth in zero-day vulnerabilities.
The report says 1 in 3 identified threat actors deploying zero days in 2021 were financially motivated, and the graph below shows a significant increase in the proportion of financially motivated actors, particularly ransomware groups, deploying zero-day exploits.
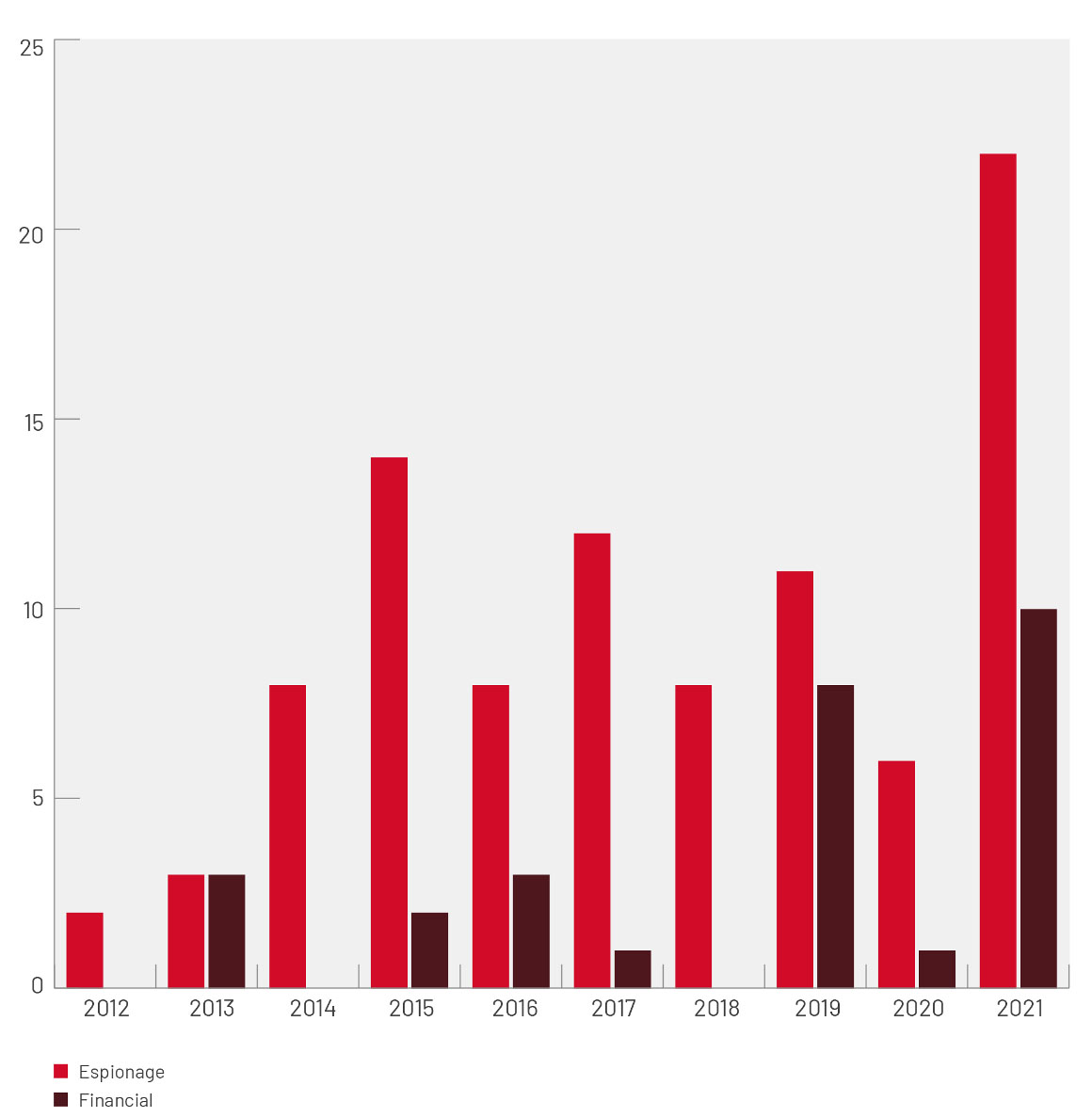
Lim says financially motivated actors are using more zero-day exploits because "having exclusive information about zero-day exploits is extremely valuable." Third-party vendors spend millions to buy zero-days from researchers, according to Lim. He says that because zero-days are "rare and unknown," it is very difficult to defend against them. "Essentially, everyone is defenseless against a zero-day," Lim says.
According to the report, threat actors exploited zero-days in Microsoft, Apple and Google products most frequently, likely reflecting the popularity of these vendors. The increase in zero-day exploitation in 2021, as well as the diversification of actors using them, expands the risk portfolio for organizations in nearly every industry sector and geography, particularly those that rely on these popular systems.
Rapid Technology Adoption
Factors contributing to the increase in the number of exploited zero-days include the move toward cloud hosting, mobile and IoT technologies, as well as the increase in the volume and complexity of systems and devices connected to the internet, Mandiant says.
As companies rapidly adopt new technologies and invest in security assets, they often have shorter time cycles to deploy. Given these time constraints, they might not have a firm understanding of the security exposure or the change in attack surface as they adopt these technologies.
"If you don't understand the technologies you are adopting, you might not be aware of misconfigurations or unpatched vulnerabilities. Some do not understand the shared responsibility model in the cloud infrastructure domain. And this lack of understanding creates a lot of loopholes in the attack surface, which is exploited by threat actors," Lim says.
Advice to CISOs
Lim says CISOs and organizations are unable to keep up with the threat landscape due to the large number of threats occurring on a very frequent basis. "They are unable to discern which ones are more applicable to their environment. The numbers are overwhelming, and the clients are not aware of what they should prioritize to patch," he says.
To help them prioritize which vulnerabilities to focus on, Lim advises CISOs and organizations to subscribe to threat intelligence reports from reputed cybersecurity vendors who have very strong research and good visibility into the threat landscape.





















