Endpoint Security , Forensics , Fraud Management & Cybercrime
Apple Fixes Zero-Day Flaws Used to Target Activist
Spyware Sold by Israel's NSO Group Linked to Attempted Attack
Apple has updated its mobile software to fix three zero-day software flaws used in an attempt to compromise a prominent United Arab Emirates-based dissident's iPhone. The attack code has been traced to an Israeli company that sells powerful hacking tools to governments - a business model that has been criticized for its potential for abuse.
See Also: Securing Your SWIFT Environment Using Micro-Segmentation: What Financial Institutions Need to Know
The code is the first publicly revealed that was capable of compromising Apple's latest iPhone software, enabling attackers to steal e-mails, SMS messages, iMessages, contact lists and application data. Security experts say these types of Apple software vulnerabilities that can provide attackers with such complete access to a target's device are highly sought after and can fetch upwards of $1 million from buyers.
The findings were revealed Aug. 25 in joint report from Citizen Lab - a research group within the University of Toronto that has published detailed investigations into the use of software exploits by governments with questionable human rights records to monitor activists and dissidents - and mobile security software firm Lookout Mobile Security.
The two organizations unwound a complicated technical trail that lead to Ahmed Mansoor, an activist who has been highly critical of the UAE government, after Mansoor shared with Citizen Lab a suspicious SMS that he received on his iPhone 6 on Aug. 10.
Targeted for Exploitation
Mansoor has long been known to be careful with electronic devices. He was targeted in 2011 by the FinFisher software made by Gamma Group, a U.K.-based organization that sold spying tools to governments. The next year, he was targeted by tools developed by Hacking Team, an Italian company in the same line of business, according to a blog post from Citizen Lab.
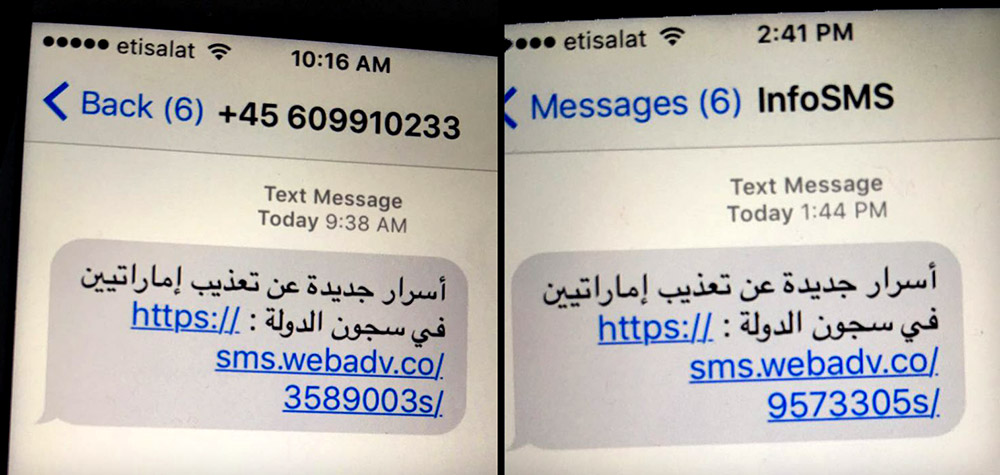
The day Mansoor received the text messages, he was running iOS 9.3.3 on an iPhone 6. Citizen Lab and Lookout found the malicious link successfully compromised an iPhone 5 running the same iOS version. They note that while the latest version of iOS at the time of the attack was 9.3.4, that is also vulnerable to the exploit.
Apple's strong security means attackers usually have to find and chain together several vulnerabilities in the mobile operating system before they can remotely compromise a device. The chain of exploits used in this attack, which researchers dubbed "Trident," starts with an exploit for a vulnerability in the browser engine WebKit, followed by exploiting two kernel-level flaws. Used together, the flaws allow for installation of an "implant," which is a euphemism for malware. The attack "happens invisibly and silently," Lookout says in a blog post.
Implant: Pegasus
The implant appears to come from NSO Group Technologies, which is based in Herzelia, Israel. In 2014, the private equity firm Francisco Partners bought a majority stake in the company for $120 million, according to Reuters.
"The implant installed by the Trident exploit chain would have turned Mansoor's iPhone into a digital spy in his pocket," Citizen Lab and Lookout say. "The spyware, which appears to be NSO's Pegasus spyware solution, was capable of employing his iPhone's camera and microphone to eavesdrop on activity in the vicinity of the device, recording his WhatsApp and Viber calls, logging messages sent in mobile chat apps, and tracking his movements."
Lookout has published a detailed technical analysis of the Pegasus spyware.
Security experts say that all iOS users should update immediately. "iOS 9.3.5 fixes some serious vulnerabilities that are being actively exploited," says digital forensic scientist Jonathan Zdziarski, author of "iPhone Forensics," via Twitter. "Drop what you are doing and update." The flaws are reportedly also now fixed in beta versions of Apple's forthcoming iOS 10.
Backlash As Governments Target Activists
Citizen Lab has published an extensive series of reports about dissidents who have been targeted by offensive cyber weapons sold by private companies to governments.
Those vendors have traditionally defended their operations by maintaining they only sell lawful intercept tools to vetted clients. But once the sales are made, the companies have little control over how the tools are used. The backlash from human rights watchers has been especially pointed.
In 2015, more than 400 GB of internal company documents belonging to Hacking Team were stolen and published. Some of those documents suggested that the government of Sudan was a customer of the company, but Hacking Team has avoided responding to related questions. Other clients of the company apparently included the governments of Azerbaijan, Egypt, Ethiopia, Morocco, United Arab Emirates, Uzbekistan, Saudi Arabia and Sudan, which many civil rights monitoring organizations say regularly violate human rights (see Spyware Vendor Alert: Suspend Software).
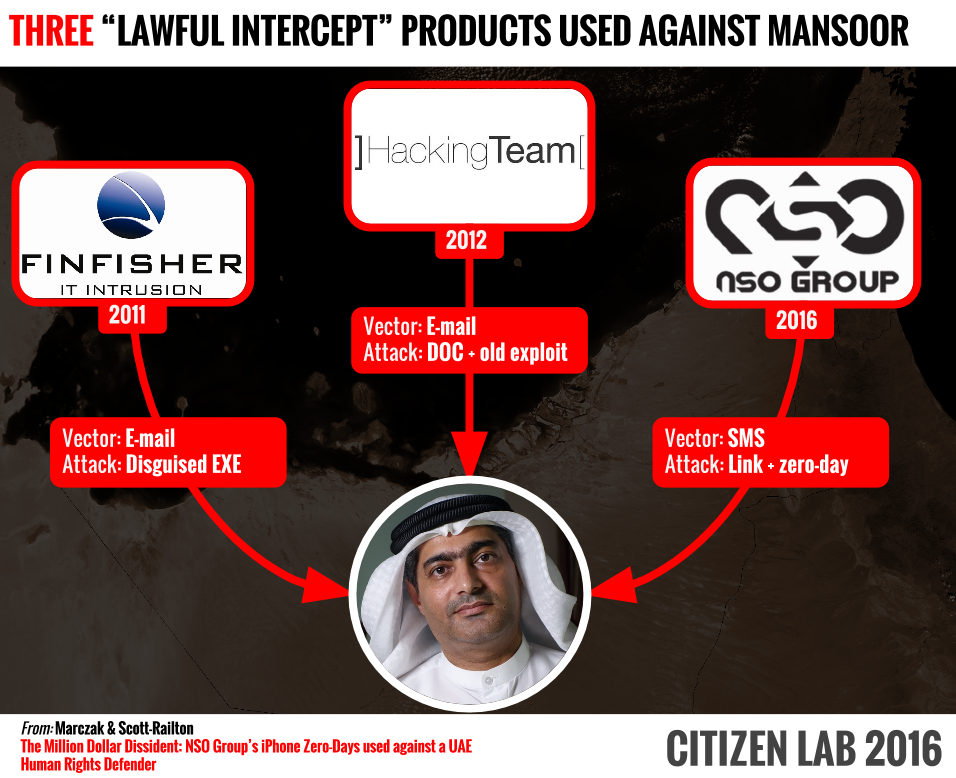
Ironically, those leaked documents provided more insights for Citizen Lab and Lookout into Pegasus, the spying software suite made by NSO Group linked to the attempted attack against Mansoor. "When we examined the Hacking Team emails leaked online after a 2015 breach, we found several instances of Hacking Team clients or resellers sharing what appeared to be NSO Group's product documentation and sales pitches," Citizen Lab says.
NSO Defends Its Sales Practices
But in a statement provided to Vice's Motherboard, NSO Group maintained that it only sells to "authorized government agencies" and complies with export control laws. The company sought to put itself at arm's length from its clients by adding it is strictly a technology company and does not operate any of its systems.
"NSO's mission is to help make the world a safer place by providing authorized governments with technology that helps them combat terror and crime," NSO Group says.
NSO Group's statement echoes a common defense of companies in its field, but one that falls flat with some security experts. "You really have to wonder what kind of human being says, 'This is how I want to make my money,'" wrote Matthew Green, a cryptography expert and associate professor at Johns Hopkins Information Security Institute, on Twitter.
Let me try this again. If some device you use a lot asks you to patch today, do it. Don't hit "later".
— Matthew Green (@matthew_d_green) August 25, 2016
Citizen Lab's and Lookout's report maintains that the latest findings show that dangerous cyber weapons continue to be sold to countries that target human rights activists, despite existing export controls.
"If spyware companies are unwilling to recognize the role that their products play in undermining human rights, or address these urgent concerns, they will continue to strengthen the case for further intervention by governments and other stakeholders," the report says.